What are the email security options? Part 2
Nov 2, 2022 | Jindřich Zechmeister
The second part of the series on email security is devoted to securing the sender's domain against abuse by spammers and fraudsters (spoofing). Messages from a properly secured domain always reach the recipient and are never spam or phishing. We will also look at the issue of message security in transit.
Prevent fraudsters from abusing your domain
The first part of the series explained that email completely lacks verification of the sender’s identity and is not immune to spoofing. What you write in the sender's name is what the email recipient will see there.
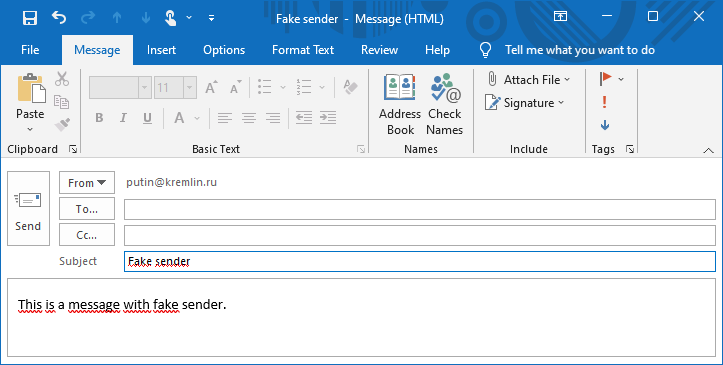
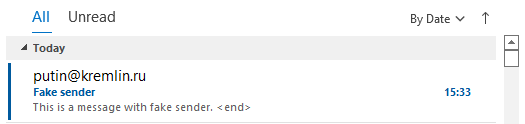
No one wants to receive strange messages with a fake sender that cannot be verified. Just remember, for example, well-known extortion emails threatening to publish videos of users masturbating if the fraudsters are not sent Bitcoin. All they needed to do was to spoof the sender's address so that users think that the email is sent from their address.
Now you will learn how to eliminate this risk and how to properly secure your mail-sending domain. By preventing spam and phishing from being sent under your name, you'll also increase the success rate of your genuine messages’ delivery to recipients.
Email Security Technology
Over the 50-year history of email, there have been many ways to increase its credibility and security. Almost half of messages sent are unsolicited spam (fortunately, the ratio is decreasing, at one time spam accounted for over 70% of all messages). Spam elimination and mail security is a topic for every administrator.
Let's get acquainted with the basic tools for mail security. Every IT administrator knows at least some of these invaluable helpers. With them, you will make using email a pleasant experience again and increase user security.
Mail Security Tools:
- SPF: using an SPF record (TXT record in DNS) you confirm to the world which servers and domains are authorized to send emails for your organization. This is the primary protection against domain misuse for spam.
- DKIM: a protocol that signs emails with a key that is in DNS and that the recipient can verify. A positive result proves that the message has not been tampered with and that the email is indeed from the sender's domain.
- DMARC: builds on SPF and DKIM. With it, you define what should happen to a message that does not comply with SPF and DKIM rules - you can quarantine it or reject it completely. When DMARC is active, reports are sent to the administrators by email, so they have control over its correct functionality or attempts to misuse the domain.
- S/MIME: a protocol and standard for message security. It provides proof of identity, digital message sealing and full end-to-end encryption. It will be described in the next part of the series.
For all the technologies mentioned above, if the information in the message header contradicts the information on the domain, then the recipient should consider such a message as spam. In the same way, tampering with the signature of the message (for example, by altering it) will be reflected by a signature error that the recipient can see (notifying him of the discrepancy).
Of course, the recipient's server (i.e. receiving mail) does not have to follow the information from the above protocols, but it is in its interest to deliver genuine messages (not spam) and keep its users satisfied.
How to use technology for security?
If you manage a mail server, it is up to you to use and correctly set up these technologies. This means you have a big responsibility because, without these technologies, users will get a lot of spam and become easy targets for phishing. However, if you set up security incorrectly, perhaps due to a lack of experience, you can jeopardize the correct delivery of mail on the domain (and in the worst case, prevent it completely).
If you are only a user and only have an email address, not access to the server, you must request the above security from your IT administrator or directly from the email service provider.
In both cases, it is clearly more advantageous to leave these worries to professionals who can guarantee you perfect email operation and security. This brings us to email service providers, including ZONER a. s. and the CZECHIA.com project. With CZECHIA.com, you can use all the above-mentioned advantages, and you also get triple protection for your mail - antivirus, antispam and antiphishing. You will be protected against spam, viruses, and fraudsters.
It is not worth worrying about the administration of emails (email servers) and it is better to leave it to the experts. Users expect and fail to appreciate a functioning service; especially with the widespread free services, it is ingrained that there is no need to pay for email. However, if something doesn't work out, for example, a message doesn't arrive, then a disgruntled customer will complain - because they don't know how email works. A layman does not know the complexity of the entire process of sending and delivering mail (see Wikipedia), so they logically do not understand the issue of email security either.
Tips for additional security
DANE, MTA-STS and BIMI are other technologies that can help mail security.
The principle of DANE is to publish the cryptographic fingerprint of the certificate in the DNS record in the domain zone, where anyone can find it and verify the authenticity of the certificate used. In the case of email services, the certificate (listed in the TLSA DANE record) is used to secure communication between servers. Trust in DANE relies on DNSSEC, which guarantees information authenticity in a domain's DNS zone.
MTA-STS is a young technology that is used with trusted certificates in the transmission of outgoing mail via SMTP. MTA-STS is simply the equivalent of DANE, but without the need to use DNSSEC.
BIMI allows the use of the sender indicator in the mail client. However, to actually use it in postal services, you need a VMC certificate. You will find more on this topic in the next part of the series.
Encryption between mail servers
Thanks to SSLmarket, you surely have your TLS certificate for your website, and site security is simple; you simply turn on HTTPS and all visitors connect using encrypted HTTPS. However, it is not that simple with emails - actually, there is no security here, it depends on the mail server administrator.
In the first part of this series, you learned that email is like a postcard that can be read by anyone on its way. The content of an email is not protected from prying eyes in any way, so you will certainly appreciate it if it is at least partially secured with TLS encryption. The servers that exchange it with each other can encrypt this communication and protect it from eavesdropping.
Can we be sure that the message is actually transmitted encrypted? Not always. Most email servers try to encrypt and use the STARTTLS protocol, but if the encryption fails, the communication will take place unencrypted (and the user has no way to influence it). So you can assume encryption, but you can't be sure. You can try to force encryption (see DANE and MTA-STS above), but message delivery always takes priority and if an encrypted connection fails, it will arrive via an insecure channel (without TLS).
Part three will be about security from the user's point of view
All the technologies mentioned above are used to confirm the authenticity of the domain from which the mail is sent, or to prevent the domain’s misuse for spam and phishing (spoofing addresses). However, it does not address the identity of the email sender themselves. We will look at this aspect and its solution next time. You will learn more about S/MIME technology, signing and encrypting emails, but also about the BIMI principle, which allows you to use the VMC certificate. As you surely know, VMC certificates allow the sender's logo to be displayed to the email recipient, and this is a promising but still young technology. Thanks to SSLmarket, you can use it too!
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
