What are the email security options?
Oct 19, 2022 | Jindřich Zechmeister
In the first part of the mini-series on email security, you will learn about the reasons why security should be addressed. Did you know that email is like a postcard that can be read by anyone who has access to it? If you don't believe me, then read on; you will certainly be convinced by the statistics on email misuse rates.
We use 50-year-old technology every day
The principle of email, like the original idea of the web, is very old. The first email was sent 51 years ago, and it would be difficult to find a similarly "popular" and durable technology (think dial-up Internet, diskettes or VHS).
Email is still the most widespread communication channel available to everyone and thanks to its ease of use, everyone knows how to use it. However, in 2022 we are still using half a century-old technology (of course with partial improvements) whose authors certainly did not foresee us using it in the way we do today. In the early days of "emailing", users did not even know spam, i.e. unsolicited mail! Today, they would certainly be surprised that we send each other emails in HTML, with large attachments and can also encrypt them.
However, the ease of using email is redeemed by zero security. It is good to realize that email does not question the communicating parties’ identities at all, and can perform under any name. This is the imperfection we have been trying to solve for decades.
Email is like a postcard that anyone can read
The creators of email never imagined it would be a messenger of secret information, and only its further evolution and modernization in the form of the S/MIME protocol enabled its security. However, security is still optional and must be taken care of by the user with the help of his mail agent.
Another major problem with email is the security of information in transit; this was not considered during design, and the MIME internet email standard itself cannot address it. You can think of an email as a sight that travels around the world and can be read by anyone who encounters it. The task of email is to transfer some information, but not to protect it and keep it secret from other users.
Emails can be protected from unwanted readers as they travel through the Internet by encryption, which takes place between the servers that forward the email message to each other. However, you are never guaranteed that mail servers communicate with each other in an encrypted manner - you can only assume so. However, encryption in transit does not address the security of the message "lying" on the recipient's server or on your computer. It can still be read by an unauthorized person because it is stored as plain text.
If you want to encrypt it and make sure it's done, then you need to "take it into your own hands" and use the S/MIME protocol to secure email messages. This allows emails not only to be signed, but also to be encrypted and keep the recipient's secret. You will find out how in the third part of our series.
Why should we secure email communications?
I believe the above information has disturbed you. The question is how much and whether it motivates you enough to be interested in the security of your mail. If this is not the case, I offer some statistics that have been brought about by publicly published research.
- An incredible 99.9% of all email is sent via the MIME protocol, which does not allow verification of the sender’s authenticity, nor does it guarantee that the message has not been altered.
- 90% of companies do not use available technologies (DKIM, SPF and DMARC) to protect their business emails.
- According to the FBI, over the past five years, damages caused by email abuse have reached a staggering $43 billion.
Private correspondence is not usually of a sensitive nature and would rarely be of interest to an attacker. For them, it is certainly more interesting to try to cheat someone in a company that they can defraud of more money.
A very common and widespread scenario is an attack on specific company employees under the name of their colleague or superior. Most users consider emails from colleagues to be safe, and they are afraid not to follow up on an email with instructions from the CEO. Thus, an attacker only needs to monitor and read corporate emails for some time (typically several months) and then target their attack appropriately.
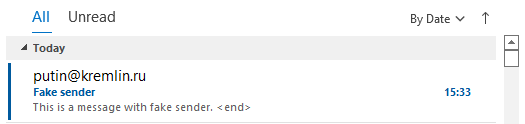
It's amazing how easy it is to send an email with a fake sender name. When sending an email, you can use any name you set as the sender, so such an attack is completely trivial and even a child can handle it. The attacker does not even need to have access to the company domain/mail. Clients accept such a message and display the set sender name, because it is not their task to check whether the message was actually sent by the declared sender.
Continue with the second part
In the next part of this series, you'll learn how you (or your IT administrators) can protect mailing addresses and the sender's domain against spam and scammers trying to impersonate you.
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
